I am trying to figure out the best way to do this…
I am seeing programs on endpoints that launch powershell scripts and CCS embedded code execution seems to be detecting it and creating PowerShell scripts in this path -
C:\ProgramData\Comodo\Cis empscrpt. However HIPS module is blocking these scripts from running because they are untrusted.
I would like the embedded code execution to be enabled, and I want CCS to detect if this code is malicious, but I also do not want HIPS alerts and popups to the end user every time HIPS blocks a script ran from this location just because the script is untrusted. What is the best way to accomplish this?
Is it wise to create a HIPS rule to set all scripts in this location to run as “Allowed Applications”? Will CCS still detect if the script is malicious and block it from executing, even if I have this HIPS rule to treat them as allowed applications?
@PremJkumar - thanks for the response. It seems that the link you provided is for the containment feature. I already have an ignore rule for containment. The alerts I am receiving are for the HIPS module of CCS. Im trying to understand the security impact of creating a rule for HIPS to set these scripts as allowed applications, or if there is a better way to allows these scripts to run but still be caught if malicious. The HIPS module is interrupting some functions of some applications and unless I click allow on the prompts everytime these things run, it prevents the application from working. It seems like the embedded code execution function of CCS is detecting the powershell scripting from the program and creating the scripts in the path I referenced and when it tries to run those scripts, HIPS alerts and will not proceed unless I hit allow.
Edit
Im assuming these scripts are being created because of the Script Analysis being enabled for powershell. if that’s true I would rather see and option for application based exclusions for script detection vs creating a HIPS rule to allow any script in that path to execute as an allowed application.
Hi @minntech,
Sorry for the misunderstanding. I will check with backend team and provide you more information.
Kind Regards,
PremJK
@PremJkumar any update on this? I seem to be able to get around the HIPS alerts by creating a HIPS rule to allow files in the “C:\ProgramData\Comodo\Cis empscrpt” path to run as allowed applications but I am trying to understand the security impact of this. Wouldnt permitting HIPS to run these scripts in this location as allowed applications be the same as disabling the Script Analysis feature for powershell altogether? Or if I allow files in that path run as allowed applications, will CCS still block them if they are found to be malicious? Want to know if I am going about this the correct way or not.
In addition to my questions above, my goal is basically to have it setup where if the process being executed by the script in this path is trusted then go ahead and let it execute, I only really care to have HIPS block the execution of processes by these scripts if they are unknown or malicious. Otherwise with the way it works by default with HIPS and Script Analysis enabled, every process these scripts try and execute seems to be generating a prompt for the end user to allow or block. It amounts to many prompts for the end user. Hopefully that all makes sense.
Hi @minntech,
We have checked with the backend team and their response was
Wouldnt permitting HIPS to run these scripts in this location as allowed applications be the same as disabling the Script Analysis feature for PowerShell altogether?
No, they are not the same. if script analysis is enabled, scripts or fileless scripts still will run in Containment, but HIPS protection will be omitted in case you create totally ignored HIPS rule for them
Or if I allow files in that path run as allowed applications, will CCS still block them if they are found to be malicious? Want to know if I am going about this the correct way or not
If the final rating is malicious, it should be detected and blocked by the AV module. but we should make sure that path is not in exclusions and AV realtime enabled.
It amounts to many prompts for the end user.
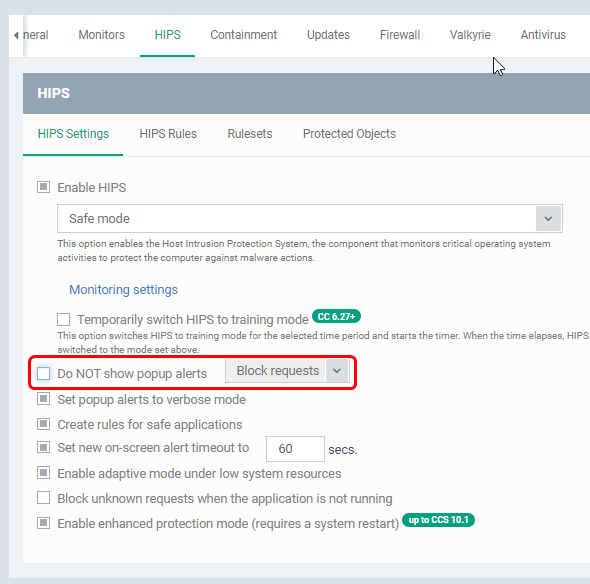
HIPS alerts can be disabled in profile settings, using the option “Do NOT show popup alerts”. Even if it is disabled, logs will be registered in HIPS logs.
Please let us know if you have any queries.
Kind Regards,
PremJK
Hi @PremJkumar - thanks for the response. I am aware of the ability to prevent popups, but when I was testing the security software out, just one program on my system, which was running legit powershell scripts to apply updates, was triggering a barrage of popups from HIPS. I believe its happening because I also have script analysis enabled for powershell. So Comod sees the scripts and creates temp scripts within its own “tempscrpt” path. However once it was running the scripts from that location, it was then triggering HIPS alerts. If I would set that option to block, then it would prevent legit applications from working. However setting it to allow I would presume means any HIPS detection would just be allowed to run?
I was trying to figure out how to strike a balance to keep HIPS on but not have it scrutinize so much legitimate scripts through script analysis. I dont know if HIPS works with ‘trusted’ files like containment does because I have trusted the scripts but HIPS will still trigger alerts. For now I have just created a rule in HIPS to ignore scripts that are ran from that comodo tempscript path. It has reduced the alerts and so far that has really been the only thing that I have seen HIPS get hung up on.