I have a client with Comodo protecting all systems and they were compromised last night. I noticed on one of the servers an itsm.bat file (which was later corrupted by ransomware, so I can’t read it) was ran, probably to bypass Comodo. So I’m not sure how they turned it off, since they did not have access to my Comodo password for the control panel, but they used a domain admin account to work around it. This company is definitely done with Comodo and I’m second guessing reselling the software after this. I can update this later with log files and screenshots. I had security settings set as per the best practices examples sent to me by Comodo support.
Hi @boiseitsolutions ,
I’m sorry to hear about this incident. We’ll check now with the team and investigate the issue. If there is anything you can provide me as to which client had this, that would be helpful. We’ll inform about the result of the investigation.
The client has hired a forensic team to fly in and analyze what they can, make copies of servers/VMs/etc, which is happening tomorrow. I thought I’d be protected even if someone was able to log on but I guess nothing protects against admin access.
If someone had cracked admin password and accessed to the system, they may be able to change many settings of course. Do you think someone had accessed that way?
The password used for the Comodo control panel was only owned by me - the account that was compromised was made by the parent company for remote access, so they couldn’t have turned it off that way.
How did they use remote access RDP? Was EDR installed on the machines? Do you have backups? Do you have span and dns filtering? What all CCS module are you using?
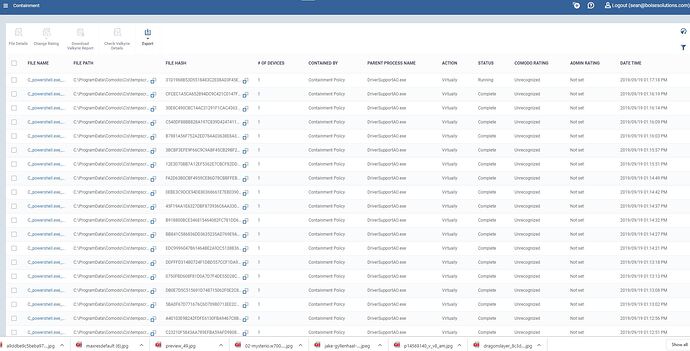
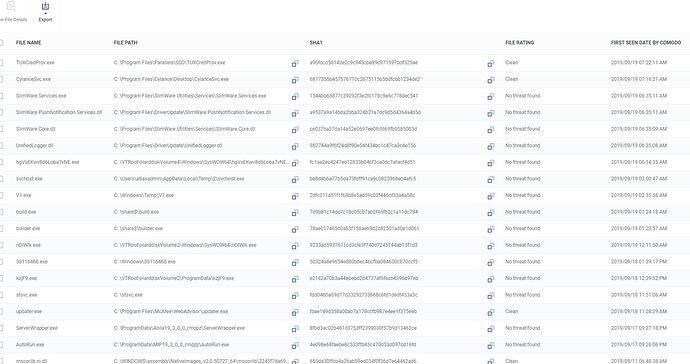
Can you show screenshots of ransomware?
@boiseitsolutions , I very much it is down to fault with Comodo product, more likely someone with admin rights has managed cripple the protection.The only time I have ever encountered ransomware on a Comodo protected PC is after the client asked for stuplidly reduced level of protection with no containment and too many folder exclusions. I would suggest running http://download.comodo.com/cis/download/installs/cisreporttool/cisreporttool.exe and also sending support copies of the profiles used. Ask first line support to escalate to L2 or L3 support - I’m sure @fatih will help you with this.
Hello Gentlemen, we have a confirmation from @fatih that @boiseitsolutions reported issue is being investigated by L3 as well as malware analysis team. L1 has contacted him as well.
Thank you and hoping to get this issue resolve as soon as possible.
I would appreciate knowing the outcome of this, please.
I too would appreciate learning what the outcome was and any details that would help us to avoid a similar infection.
shoulda woulda coulda, agree Comodo should have been able to stop this but, this is where Business continuity and DRaaS solutions are a must.
EVERY protection you put in place will eventually get bypassed. Solid backup with offsite and DraaS if customer cannot be without systems for any length of time.
And for less than a cup of coffee per day, per server you’d be mad not to ?
Update, please?
Hi all
let me update everyone about this issue: the incident is being analyzed by our teams as soon as we were notified by this post together with the customer. It’s been experienced that there were a couple of different conditions that lead to this infection, in which the most important one is the profile which was applied to devices did not have Auto-Containment turned on and this is confirmed with the customer. Another condition is CCS not being running on one of the device identified on the network, which is potentially the source of Malware spreading through the network.
All CCS devices configured and running properly were protected.
Can you post a link to the recommended settings here?
We have default profiles already provided on the system. These are the best option to start with. All of them have Auto-Containment set on.
There are a couple of them, you may chose one depending on the environment you have, other products you have or other security measures you already took. If you need personal assistance, please get in touch with our customer support, they will provide you the best option.
If auto containment was not in use, then surely the blame can’t be attributed to Comodo. As mentioned in my earlier post, when one of our clients insisted in Containment being disabled they also picked up a ransomware infection.
yep, an example of ransomware blocking, fresh from one of our customer: https://forum.itarian.com/forum/products/endpoint-protection/38021-omnisphere-ransomware-ko-css-wins