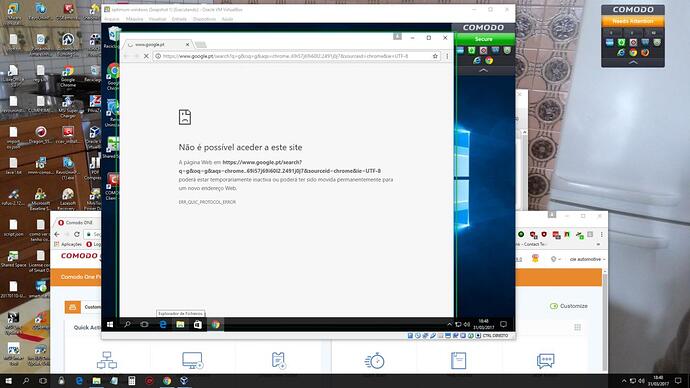
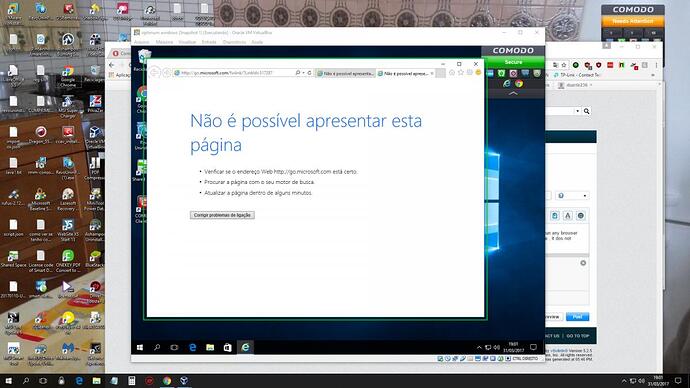
Good day to all i noticed something , that it should not happen witch is this : machines using the hardened windows profile from itsm are having a problem ,if a user chooses to run any browser sandboxed, browser opens but than the user can`t browse normally has they without using them sandboxed, this only happens using the hardened windows profile in the machine , it dos not happen using the others windows profiles from itsm , if someone knows how to fix this please say it , thank you all!
Thank you for the info Mr Riley , but this isnt supposed to happen ? or is this a normal behavior using this profile ? if it isnt it should be fixed ? thank you!
Hi @duarte236
Sorry for the previous responses. Hardened profile template has higher restrictions than other templates by default. It requires more customization based on your needs.
On hardened profile template, we don’t let any application that is contained to make network communication. This would prevent any unknown application to get some data from device and upload it to internet or some other network space. This would eliminate any data stealing possibility or lateral movement.
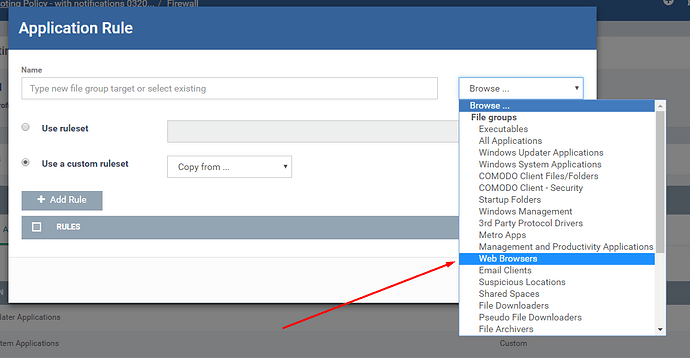
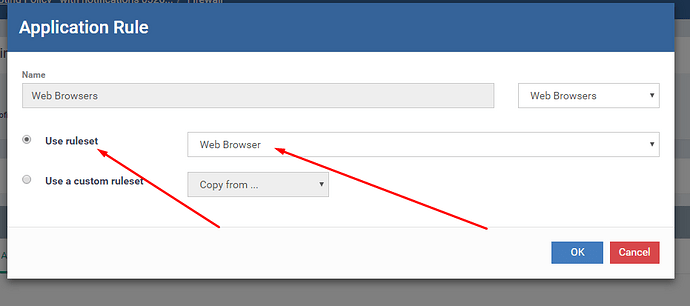
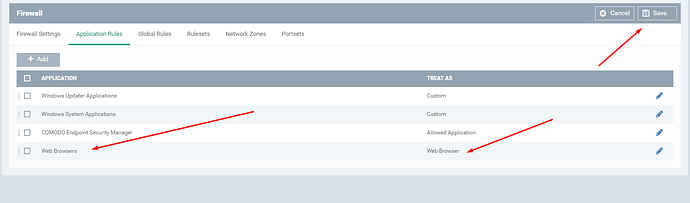
For this specific issue, you need to define web browser applications specifically to be allowed under firewall if you want them to be able to communicate with internet even when they are contained. Details here: Firewall Settings, PC Firewall, Firewall Protection, Endpoint Manager
I am adding a few screen shots to explain you easier steps.
Please let us know if we can help with anything else or any further question.
Ilker
Thank you very much for your answer , i do understand why you have set this rule in hardened profile for security reasons , before i saw this info that you have provided i already made some changes at the firewall and i was able to get sandboxed browsers to connect, anyway i wanted to thank you for your kind help!.