I heard there is due to be a hotfix release this weekend, primarily for patching. Is this still the case?
Hi @nct
We had a CRT over Service Desk yesterday to address some issues that was effecting limited customer base. However, there wasn’t a CRT for patch management. Apologies if any misleading communication before. Please ask an update over ticket number if you were waiting for any particular fix.
Ilker
Hey nct, are you having patch management issues also? I wonder if you symptoms are the same as mine. I have a ticket open and I believe they are working on it, so perhaps it’s the same issue, but any newly added machines (last 3 weeks roughly) show “No results.” in OS patching in ITSM. Third party patching is working fine. Generally it seems no updates are coming into OS patching in ITSM from endpoints - I had a machine that was upgraded to Windows 10 and a week later it was still showing Windows 7 patches available. Newest patch showing in the global Patch Manage tab in ITSM shows April 20th, I’m sure there are updates available since then. So it seems as if something is broken where ITSM can’t communicate with windows update on any of the clients (so I’m thinking this is more likely to be a backend issue than a client issue, but who knows, maybe a Comodo client update broke this?). I’m starting to get a bit worried since we commit to being strict about patching with customers, wondering if I should request a Procedure to run all critical updates if there are any using Windows update (I just won’t know if it worked or not maybe?)
@indieserve We don’t use patch management ATM, just anti virus.
Comodo’s AV suite is the best. It’s what brought me back after trying some other RMMs last year. Thankfully the rest of C1 has come up to speed pretty quickly. I’ve seen patch management issues with other RMMs, I’m confident they’ll get it sorted out, just makes me nervous not having applied patches in almost 3 weeks.
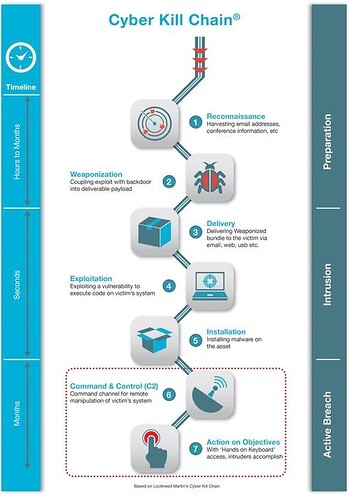
just a litte insight…no matter what app is unpatched…these unpatched apps represent “explotiation” and “Installation” stages of a “killchain” where the attacker has to run an “executable” of some sort in the endpoint. Thanks to our endpoint protection this happens inside “containment” (https://enterprise.comodo.com/cpu-en…ualization.php ) .
So you can breathe easier if you have Comodo protecting you and you haven’t patched applications. ![]()
True, but I have one customer who has random IT audits by one of his major customers, and right now I may be out of compliance, I have no idea. Anyway, mkannan is writing me up a script to manually (with windows update) apply any critical patches, so that should suffice for now until they figure out the patch management issue. Thanks Melih!
I agree, compliance etc are all important.
I am asking questions internally to speed this up. Step by step, we are becoming bigger and better partner for our partners…thank you for your patience! (btw…i have a 4pm EST meeting today to discuss the Korugan firewall requirements for you ![]() , do expect us to reach back to you soon ).
, do expect us to reach back to you soon ).