In ITSM, setting a file as trusted can be done in two ways,
- Application Control
- Device List
1.Application Control:
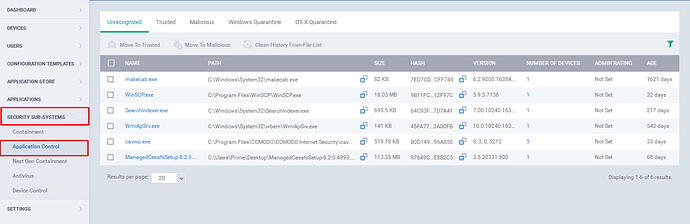
Step [1]: Go to ITSM -> Security Subsystems and then Click “Application Control” Menu.
Step [2]: The ITSM has grouped the files into three main categories, and the categories are
-
Unrecognized
-
Trusted
-
Malicious
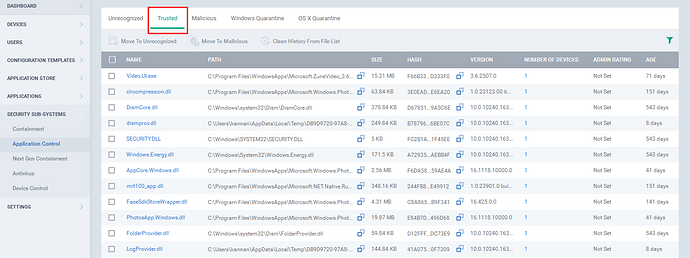
Step [3]: Go to Trusted tab.
Step [4]: The Trusted files from all the enrolled endpoints will be listed here.
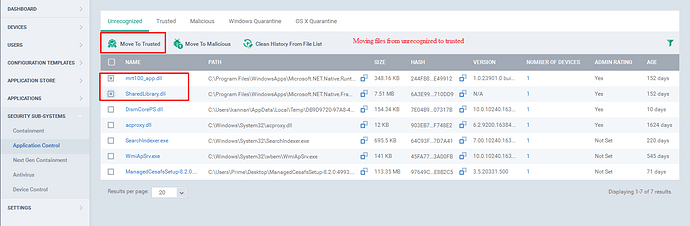
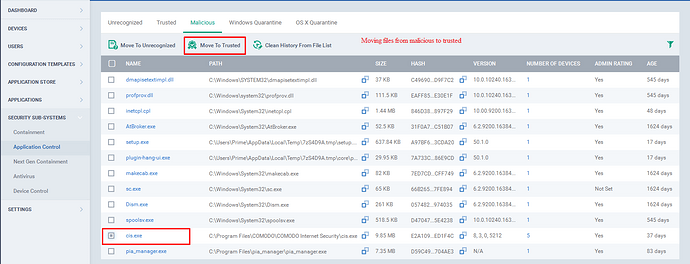
Step [5]: If you find a file from the unrecognized tab or Malicious tab as Trusted, then you can move the file to Trusted.
Step [6]: To Move the file(s) to Trusted tab,
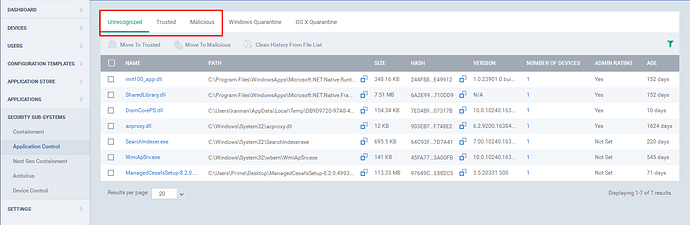
a) Go to Unrecognized tab or Malicious Tab.
b) select the check boxes of the appropriate files.
c) Click the “Move to Trusted ” option at the top.
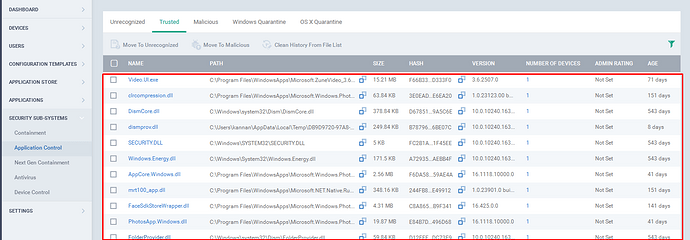
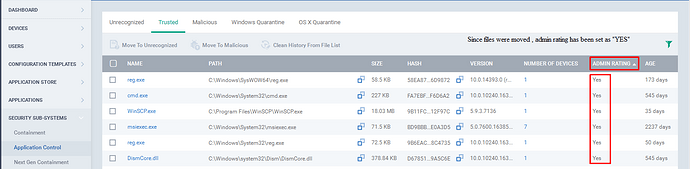
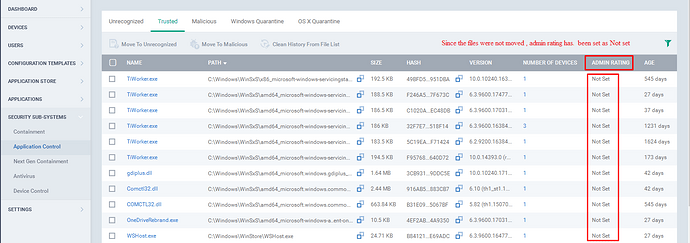
Step[7]: The Admin Rating, Indicates whether the file was manually moved by the Administrator from one category to another and the Categories are Unrecognized, Trusted and Malicious.
1.If Admin Rating is “yes”, Indicates that the file was moved by Administrator.
Example: Since the files were moved, the admin rating is set as “yes”. (Please Refer the screenshot)
2.If Admin Rating is “Not Set”, Indicates that the file was not moved by Administrator.
Example: Since the files were not moved, the admin rating is set as “not set”. (Please Refer the screenshot)
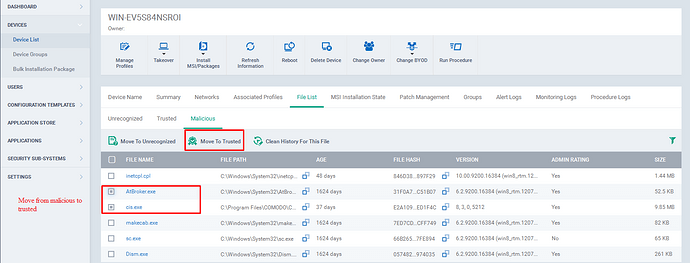
2.Device List:
Step [1]: Go to ITSM -> Devices and Click “Device List ”Menu.
Step [2]: Select a device from the list.
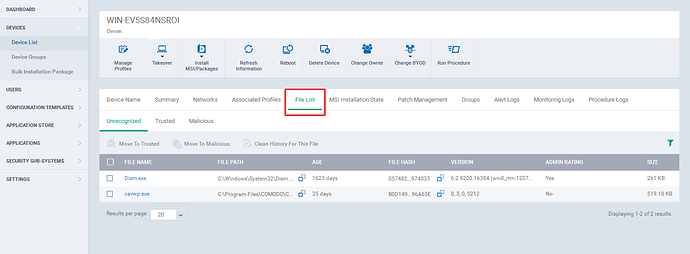
Step [3]: Go to File List tab.
Step [4]: If you find a file from the unrecognized tab or Malicious tab as Trusted, then you can move the file to Trusted.
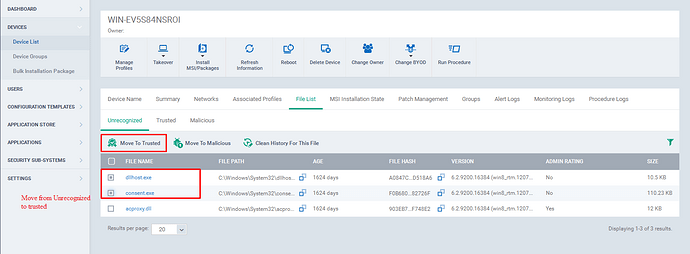
Step [5]: To Move the file(s) to Trusted tab,
a) Go to Unrecognized tab or Malicious Tab.
b) select the check boxes of the appropriate files.
c) Click the “Move to Trusted ” option at the top.
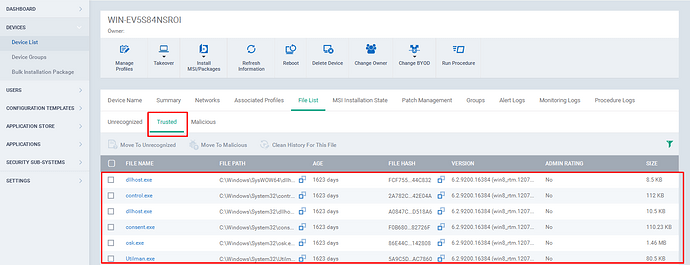
Step [6]: Click on the trusted tab.The trusted files that are in a device will be listed here.