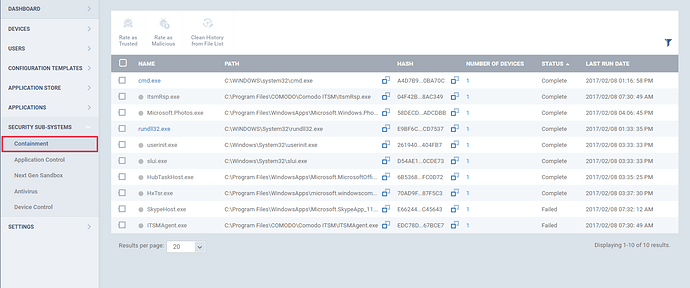
The rules that are set in the containment profile section identifies certain applications/files in the device.Such files will be listed under “Containment” menu in the ITSM. The containment provides a protected environment to run such unrecognized application.The advantage of running from the containment is, the applications are not allowed to access the data on the remote machines.
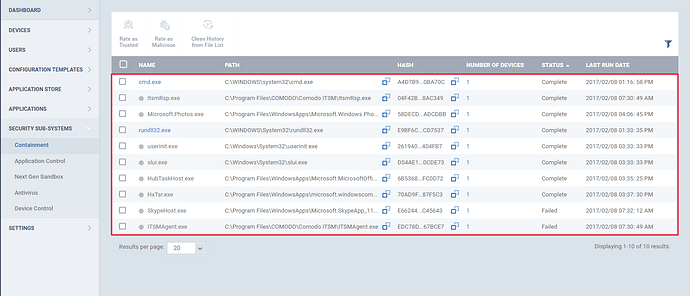
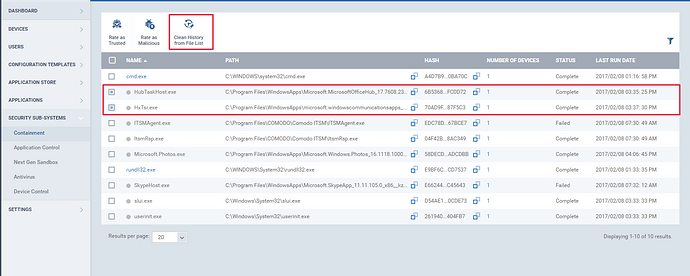
Step [1]: Go to “Security Sub-Systems” and select “Containment” menu.All the containment files will be listed in here.
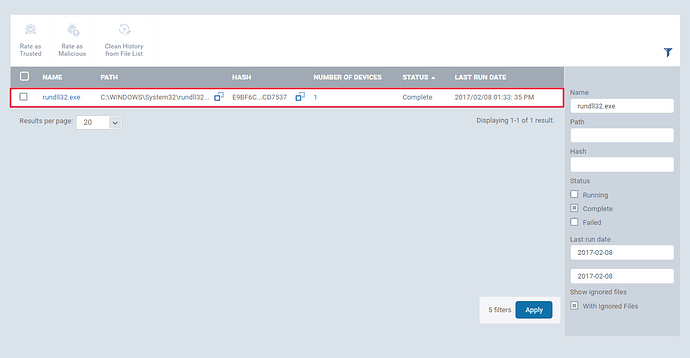
Step [2]: The files can be filtered and sorted out using the filter option.To apply filters, click the funnel icon
fill the form and click “Apply” button.

Illustration
1.Name - Enter the name of the file.Example :rundll32.exe
2.Path - Enter the path.
3.Hash - Enter the hash value.
4.Status - Provide the status. Example:Complete
5.Last run date - Provide the last run date. Example : From :2017-02-08 To:2017-02-08
6.Show ignored files - Choose the check box, to display the Ignored files.
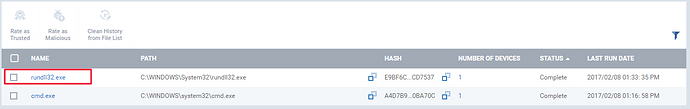
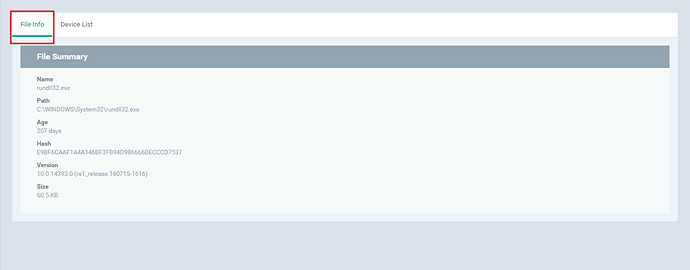
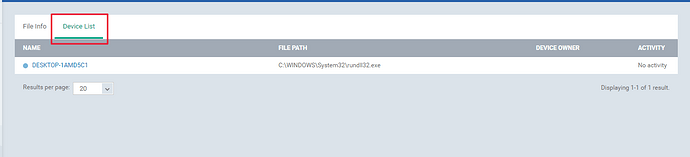
Step [3]: Click on the name of the file, view the details on “File Info” and “Device List”.
1.File Info - The detailed information about the file such as “Hash value”,”age ”,”version” will be available here.
2.Device List - The details of the device will be mentioned here.

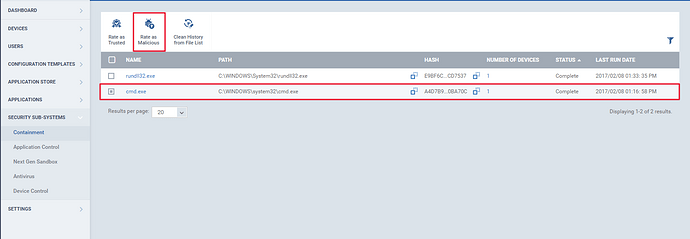
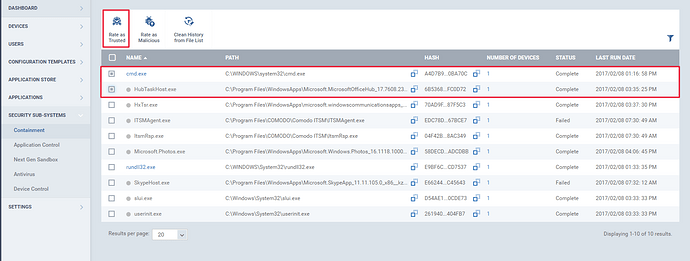
Step [4]: A file can be rated either as “Malicious” or “Trusted”. To rate a file, select the check boxes of one or more files and click “Rate as Trusted” or “Rate as Malicious”.
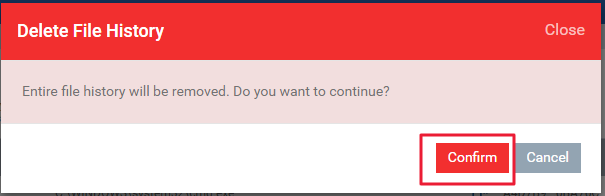
Step [5]:A file can be removed from the contained list by clicking the name of the files and click the “clean history from file list” button, a “Delete File History” prompts open and then click confirm button. Thus file will be removed.
![]()